Fortunately, I have recently discovered a great way to create Azure AD App Registrations using the Azure CLI 2.0. This also includes adding any permissions the app requires on resources e.g. Microsoft Graph, Office 365 SharePoint Online etc. This has not been previously possible with the Azure AD PowerShell Cmdlets.
So in this post, let's go through what is needed to achieve this:
First, you need to have the Azure CLI 2.0 installed on your machine. Follow this link to get it if you haven't already:
https://docs.microsoft.com/en-us/cli/azure/install-azure-cli?view=azure-cli-latest
Once you have the CLI, here is the code to create an Azure AD App Registration including the required permissions:
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| az login -u $adminUserName -p $adminPassword | |
| az ad app create --display-name $azureADAppDisplayName ` | |
| --identifier-uris "https://$tenantDomain/$uniqueGUID" ` | |
| --reply-urls "https://$functionAppName.azurewebsites.net/.auth/login/aad/callback" ` | |
| --required-resource-accesses "$executingScriptDirectory/AADApp/requiredResourceManifest.json" |
This file contains bidirectional Unicode text that may be interpreted or compiled differently than what appears below. To review, open the file in an editor that reveals hidden Unicode characters.
Learn more about bidirectional Unicode characters
| [ | |
| { | |
| "resourceAppId": "c5393580-f805-4401-95e8-94b7a6ef2fc2", | |
| "resourceAccess": [ | |
| { | |
| "id": "594c1fb6-4f81-4475-ae41-0c394909246c", | |
| "type": "Role" | |
| }, | |
| { | |
| "id": "e2cea78f-e743-4d8f-a16a-75b629a038ae", | |
| "type": "Role" | |
| } | |
| ] | |
| }, | |
| { | |
| "resourceAppId": "00000002-0000-0000-c000-000000000000", | |
| "resourceAccess": [ | |
| { | |
| "id": "311a71cc-e848-46a1-bdf8-97ff7156d8e6", | |
| "type": "Scope" | |
| } | |
| ] | |
| }, | |
| { | |
| "resourceAppId": "00000003-0000-0000-c000-000000000000", | |
| "resourceAccess": [ | |
| { | |
| "id": "5b567255-7703-4780-807c-7be8301ae99b", | |
| "type": "Role" | |
| }, | |
| { | |
| "id": "7ab1d382-f21e-4acd-a863-ba3e13f7da61", | |
| "type": "Role" | |
| } | |
| ] | |
| }, | |
| { | |
| "resourceAppId": "00000003-0000-0ff1-ce00-000000000000", | |
| "resourceAccess": [ | |
| { | |
| "id": "678536fe-1083-478a-9c59-b99265e6b0d3", | |
| "type": "Role" | |
| } | |
| ] | |
| } | |
| ] |
Trusting the App:
Update (5th April 2019):
The Azure CLI now has a command to grant the app permissions on behalf of the admin as well
https://docs.microsoft.com/en-us/cli/azure/ad/app/permission?view=azure-cli-latest#az-ad-app-permission-admin-consent
az ad app permission admin-consent --id [--subscription]
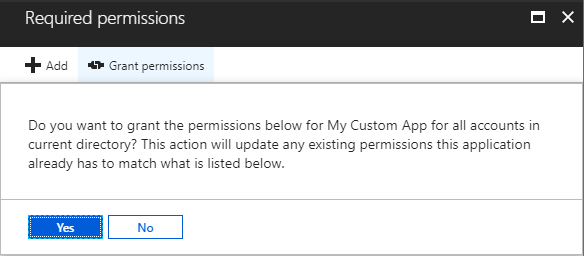
If you still want to use the portal to grant the permissions you can do so as an Admin by going to the app and clicking on the "Grant Permissions" button:
For more possibilities with the Azure CLI 2.0, checkout the reference: https://docs.microsoft.com/en-us/cli/azure/reference-index?view=azure-cli-latest
2 comments:
Hi
Your blog post is really helpful.
Could you explain more on what is expected for uniqueGUID and executingScriptDirectory please.
If I already created an new webapp service where can I get those parameters from?
Thanks!
Nice article mate. Very helpful.
Recently I noticed that there is a command for admin consent - https://docs.microsoft.com/en-us/cli/azure/ad/app/permission?view=azure-cli-latest#az-ad-app-permission-admin-consent
Example usage might be
$appId = $(az ad app list --display-name $azureADAppDisplayName --query [].appId -o tsv);
az ad app permission admin-consent --id $appId;
Post a Comment